Doesn’t it feel like yesterday when the world was roaming around letters and telegrams to contact someone? But look at the current scenario where everyone is so digitally advanced that they cannot even think of living without their devices. In other words, we can say it like this the data serves as the lifeline of the business organizations. Technology is continuously expanding its horizon and leading to new innovations. But with this expansion, we can also expect an equal expansion of cyber issues or threats. So this indicates that the market demands robust cyber-secure software that can lead to actual business growth. The more advanced the technology becomes the more the cyber criminals are seeking to introduce various vulnerabilities to the market.
Which can vary from phishing scams to ransomware attacks. This can result in harming software integrity, loss of confidential information, and other business losses. The term cybersecurity compliance is defined as protecting standards and requirements. Which are introduced by some agency, law, or government authority. These standards and compliance experts work on protecting organization’s majorly working in terms of data.
 Source: Resource Mordor Intelligence
Source: Resource Mordor Intelligence
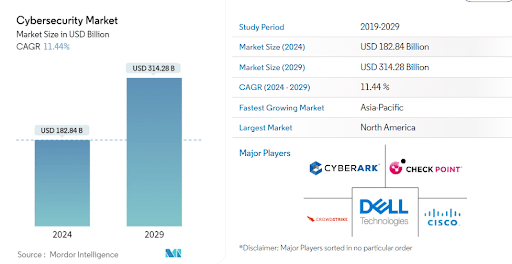
This highlights that the cybersecurity solution market needs to be upgraded with new techniques and innovations for the prevention of any cyberattack. The research data by Mordor Intelligence, 2023, highlights the same aspects of the cybersecurity framework market. As shown in the above figure the cybersecurity market is estimated to attain USD 182.84 billion in 2024 and is expected to reach at USD 314.28 billion in 2029. This shows a compound annual growth rate of 11.44% from 2024 to 2029. This shows how rapidly the cybersecurity market is expanding and providing enhanced security in the software industry.
Blog Highlights
In this blog, we will work on presenting every important aspect of cybersecurity compliance for a secure software future. The major highlights of this blog are major advances in integrating cybersecurity compliance along with an analysis of major cybersecurity compliance regulations. Give this blog a quick read and explore how important this security & compliance services can be for your running data business.
Advantages of Implementing Cybersecurity Compliance
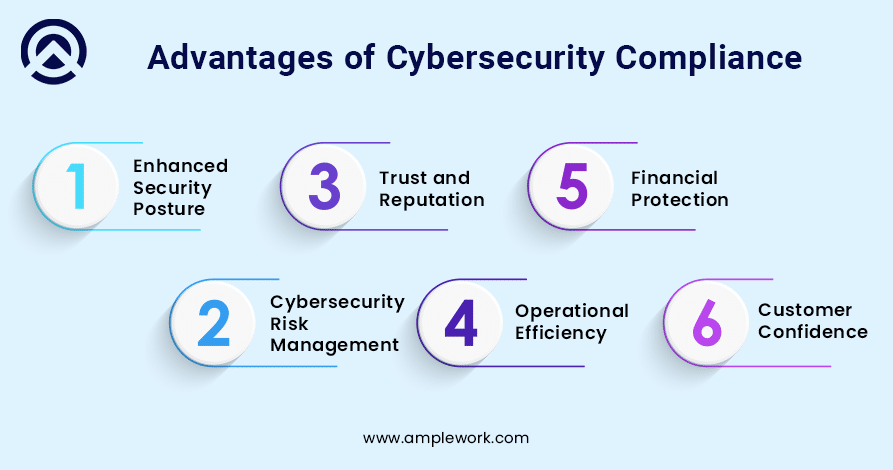
1. Enhanced Security Posture
While working in an environment, one needs to take care of compliance and regulations. These can be implemented straight to the process, the encryption, access control, and regular vulnerability assessment. The emergence of these practices results in securing the whole organizational process and practices. Along with this, opting to ask for what are the requirements for cybersecurity. leads to saving the organization from potential fines and legal issues. These compliance frameworks work on dealing with the incident response. And disaster recovery of the issues caused by cyber security policies. This compliance works on spreading awareness of security awareness and implementing continuous improvement.
2. Cybersecurity Risk Management
Integration of compliance in cyber security makes sure that the application does not meet any cyber vulnerabilities. With these organizations can prevent issues like data breaches, malware attacks. And other severe issues related to the secure process of applications. With the emergence of compliance sensitive data can be saved as well as it enhances the organizational reputation and consumer trust. These practices ensure that the applied cybersecurity solutions are properly synchronized with the industry standards and best practices. In this process, the organizations can look forward to implementing a comprehensive risk management strategy. That works on minimizing the disruptions an financial losses.
3. Trust and Reputation
The integration of cybersecurity compliance results in enhancing organizational reputation and majorly building the trust of users. These compliance standards become mandatory to save the organization from fines, operational shutdowns, and legal penalties. This is recognized as the organization’s non-compliance and not serious in providing secure cybersecurity solutions to their customer as this can harm both of the mentioned factors. A proper follow-up of the compliance standards can result in trust maintenance, increased reputation, and competitive advantages. Staying up to date with following security compliance makes the organization’s processes stay ahead of emerging threats and issues. This approach not only works on making the app safe but also makes it achieve success on a long-term basis.
4. Operational Efficiency
A compliance framework involves proper guidelines for efficiently responding to the cyber threat and a complete recovery. This shows the effective nature of security compliance toward enhancing the efficiency of the application operations. It further provides the advantages of quick response to cyber security threats, continuous growth to the business, and minimized downtime. The emergence of a compliance management system provides a structured procedure. In which the identification, containment, and mitigation of security breaches become easy and helps reduce the potential impact of incidents. This emergence of different advantages results in coordinated efforts among different departments that enhance the overall work efficiency.
5. Financial Protection
Cyber security attacks can affect the business into significant financial losses due to the loss of data sets. It helps businesses from going through financial losses like the amount invested within the security breaches associated with the recovery of products. By approaching establishing security standards and practices, organizations can recognize and resolve vulnerabilities before they become more harmful. This results in minimizing the direct financial losses and also reduces the indirect losses like reputational loss and customer churn. Along with this the integration of cyber security compliance standards involves the facility of cyber insurance. This work provides an additional safety net overall while maintaining compliance as a critical investment for finances and stability.
6. Customer Confidence
Aren’t we living in a digitally transformed world, then we can expect consumer requirements in the most advanced way. The current consumer environment is way more concerned about their personal information and its security. The integration of these compliances provides appropriate security to such requirements and provides cyber security solutions according to the requirements. With cybersecurity compliance, personal information can be secured with responsibility while enhancing consumer confidence and loyalty.
Major Cybersecurity Compliance Regulations
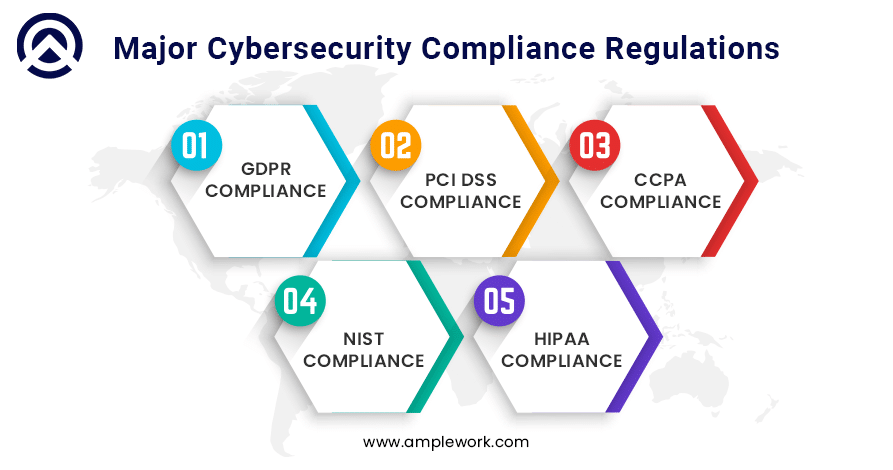
General Data Protection Regulation (GDPR)
This standard was implemented by the European Union in 2018, this work on setting compliance regulations straight for the organizations handling data of the EU individually irrespective of their location. It is constructed in seven core principles such as lawfulness accuracy, data minimization, fairness & transparency, limited storage, integrity, purpose limitation, confidentiality, and security. These principles make sure that the personal data is connected, processed, and stored responsibly having a clear purpose and accurate security measures in place. The compliance standards aligning with GDPR compliance solutions provide safety to individual and their privacy rights, working on saving one from different penalties for noncompliance. It also shows the importance of data protection in this digital age.
Payment Card Industry Data Security Standards (PCI DSS)
It is defined as the set of regulatory standards for ensuring all organizations work on maintaining a secure environment for credit card information. This compliance has conditions like annual validation of the compliance and follow-up to its six principles. These are constructing and maintaining a secure network, providing protection to cardholder details, managing compliance management systems, implementing strong access control measures, regular monitoring and testing of networks, and managing an information security policy. These PCI DSS compliance solutions help organizations safeguard cardholder data and work on ensuring robust security practices.
California Consumer Privacy Act (CCPA)
This is an important piece of legislation that grants consumers in California for having greater control over their data which is collected by different organizations. In other words, it makes organizations disclose their data privacy practices to their product users. It also works on offering several rights to them such as the right to know, deletion, protection against discriminatory practices, and opt-out of sale. These CCPA compliance solutions are applicable to many organizations and work on setting clear requirements for data transparency and consumer choice. With the integration of compliance, users can make sure that they hold the right to ask how their data is utilized.
National Institute of Standards and Technology (NIST)
This NIST cybersecurity framework works on promoting innovations and industrial competitiveness with the help of technology standards. In this, the NIST 800-53 risk management framework provides guidelines for managing information security systems. In the initial stage, it was applicable for US defense and contractors but currently, it is adopted by enterprises globally. The NIST 800-161 works on processing and resolving the risks involved in the operations of the information and communication technology supply chain. These frameworks ensure the organization enhances security, manages risks, and ensures risks in its technically advancing system.
Health Insurance Portability and Accountability Act (HIPAA)
This is denoted as one of the critical legalization-ensuring factors like confidentiality, availability, and integrity of protected health information (PHI). This framework is majorly applied in healthcare settings, including providers, clearinghouses, plans, and relevant business professionals. The emergence of this framework mandates strict compliance with its privacy standard. The best cybersecurity company provides proper follow-up for the companies to follow these compliances. This HIPAA compliance works on cybersecurity risk management like cyber attacks. It also fosters trust between patients and healthcare organizations. This shows the importance of confidentiality and integrity while managing sensitive healthcare information.
Conclusion
The implementation of cybersecurity best practices is mandatory in the current technical environment. As this work on safeguarding essential and sensitive data, builds consumer trust, enhances security, mitigates cybersecurity risk, and increases consumer confidence. Organizations make sure to apply compliance standards to gain improved operational efficiency, competitive edge, and protection of financial health. With the integration of these practices and a culture of security awareness, businesses are not only strengthening their reputation but also enhancing their stakeholder relationships. In other words, cybersecurity compliance is a strategic imperative that works on supporting long-term success in the digitally advanced world.